Setting Up a Malware Analysis Lab
Setting Up a Malware Analysis Lab Free Tutorial Download
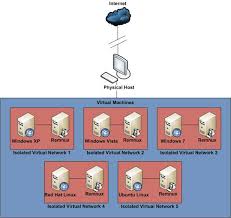
As an organization or individual, you may be curious to find out what a malware does: whether it collects and sends back data to a host, how it gets to a machine among other activities. This may not be possible if you are using your work laptop or personal laptop that contains sensitive information. Some do not have a way of accessing another machine and this makes it difficult for us to carry out malware analysis or you may be discouraged getting into the malware analysis field. With the presence of hypervisors and other tools such as fakenet, there are ways of securing your computer.
Disclaimer: I would highly recommend carrying out keen and careful configurations for this so as not to make any mistakes that may open a path for malware to leak into your main computer.
Requirements
- Laptop or desktop — this is what you will be working on.
- Up-to-date hypervisor such as VirtualBox, VMware etc — these hypervisors will help create an isolated environment for you to work on.
- Windows 10 or 7 ISO
The first step is to download a hypervisor and install it onto your machine. When downloading the hypervisor do not install the guest additions. Remember we are trying to isolate this environment as much as possible so as to avoid malware leaking.
Then download a legitimate Windows 10 or 7 ISO. The download speed will depend on how fast your internet is. After having these, create a new virtual machine and set the settings to your desired specifications and include the ISO file that will be used with that virtual machine.
When setting the virtual machine settings such as disk space, number of RAM, number of processors, storage network etc. make it as real as possible depending on your system resources. I insist for one to do this as most malware today is designed with anti-analysis features that will prevent you from analyzing it by detecting the environment.
After everything is set up, run the system. In the system, before we turn the network interface to host only adapter, we have to install the third-party tools, debuggers and all tools that we need for the analysis or threat analysis. This process can also be done before and all you have to do is to create a shared folder. Remember to set up everything since during the analysis, we will not have any active internet connection and also, we will have disabled the shared folders.
Fakenet is a tool that will allow you to intercept and redirect all or specific network traffic while simulating legitimate network services.
You should always disable Windows antivirus and updates on the virtual machine. The antivirus will always capture the malware as malicious and corrupt it hence prevent you from using it.
As much as we may have everything set in place, it is important to make the system look real as possible. This can be achieved by installing programs such as Chrome, WinRAR and others that users use every day. This prevents the malware from knowing that it is in a virtual environment.
Once fakenet is downloaded, open the folder and run the executable as an admin. Fakenet requires admin privileges for it to run. It will automatically load up the command prompt and you can then see the requests that when you open up a browser, the fakenet success page should have loaded up.
MUST REMEMBER
- Be Keen so that you do not infect yourself
- Set the virtual machine network to host-only adapter (after installing)
- After installing or sending everything you need including the malware, then turn off the shared folder
- Use up to date software, hypervisor and ISO files.
- Disable windows antivirus and windows updates
Important Links
- Fakenet
Download Setting Up a Malware Analysis Lab Free
https://xmbaylorschool-my.sharepoint.com/:u:/g/personal/grayem_baylorschool_org/EeBgrhhprwBNr54YMzbYsrMB0tUbElyMJXnmciABZmLQEA
https://bayfiles.com/hflaAeUco0
https://drive.google.com/file/d/1AxZKcVHdqZF7Gh4rZEFmiB6CrBKiW9ZO/view?usp=sharing
https://drive.google.com/file/d/18SohwvJDL6fyOdsvhmt1Iy8a9bAnEcAi/view?usp=sharing
https://uptobox.com/cdpnqix9fd0d